Encryption is the default for on-line communication, with practically all net visitors protected by safe protocols like TLS/SSL. But, as encryption turns into extra ubiquitous by the day, so do the alternatives for risk actors to take advantage of encrypted channels.
The identical encryption that safeguards reliable actions additionally acts as a conduit for malicious ones. Attackers are utilizing encrypted channels to bypass conventional defenses, concealing malware, phishing campaigns, cryptomining/cryptojacking, and knowledge theft inside encrypted visitors.
The Zscaler ThreatLabz 2024 Encrypted Attacks Report examines this evolving risk panorama, primarily based on a complete evaluation of billions of threats delivered over HTTPS and blocked by the Zscaler cloud. The report highlights the more moderen tendencies, high risk classes, most typical targets of encrypted assaults, and different insights into how attackers are weaponizing encrypted visitors.
5 key findings on encrypted assaults
The ThreatLabz analysis workforce analyzed 32.1 billion encrypted assaults blocked by the Zscaler cloud between October 2023 and September 2024 to determine and perceive the newest risk patterns. The next subset of findings highlights among the most distinguished tendencies and targets.
1. Regular development in encrypted assaults: The Zscaler cloud blocked an unprecedented quantity of assaults embedded in TLS/SSL visitors in the course of the evaluation interval. Encrypted threats accounted for 87.2% of all blocked assaults, representing a ten.3% year-over-year improve in encrypted assaults and reflecting the rising reliance on encryption by risk actors to cover their malicious actions.
2. Malware dominates the panorama: Malware stays essentially the most prevalent encrypted risk, representing 86.5% of blocked assaults. This development highlights the variation of malware techniques to thrive in encrypted channels, utilizing encryption to masks payloads and evade conventional safety and detection measures.
Zscaler
Determine 1: Prime risk classes noticed
3. Cryptomining/cryptojacking, cross-site scripting, and phishing threats surge: Cryptomining/cryptojacking and cross-site scripting (XSS) are among the many fastest-growing encrypted threats, with year-over-year will increase of 122.9% and 110.2%, respectively, whereas phishing noticed a notable 34.1% soar. It’s doable that these spikes had been fueled by the rising use of generative AI applied sciences, which make it simpler to create superior cryptomining scripts, automate malicious XSS scripts, and execute extremely convincing phishing campaigns.
4. Manufacturing tops checklist of most impacted industries: The manufacturing, know-how, and providers industries had been essentially the most focused, with manufacturing enduring 13.5 billion encrypted assault makes an attempt between October 2023 and September 2024.
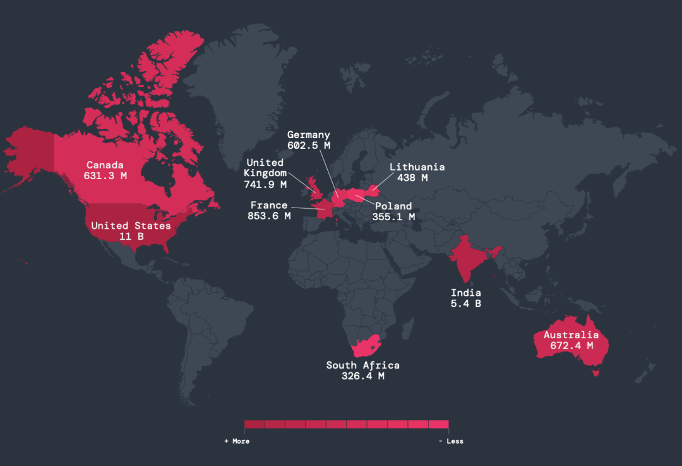
5. The US and India stay high targets: Receiving 11 billion (US) and 5.4 billion (India) encrypted assaults in the course of the ThreatLabz evaluation interval, the US and India retained their positions as essentially the most focused nations, adopted by France, the UK, and Australia.
Zscaler
Determine 2: A map of the nations that have essentially the most encrypted assaults
Evolving encrypted assault tendencies
ThreatLabz uncovered many important evolving tendencies in encrypted assaults, from attackers leveraging encryption channels to siphon off delicate knowledge to adversary-in-the-middle (AiTM) strategies utilizing superior instruments and TLS/SSL encryption to create practically undetectable phishing campaigns. The report affords examples of every.
One notable development explored intimately by ThreatLabz is the rising abuse of cloud providers by superior persistent risk (APT) teams. By mixing in with reliable cloud providers visitors, APT teams can reap the benefits of the default use of TLS/SSL encryption enabled to assist them evade community safety controls. ThreatLabz delves into this development, offering an in depth evaluation that features:
- Prime APT teams abusing cloud providers
- Prime 10 cloud providers abused
- Prime providers abused for payload supply
- Commonest techniques utilized in cloud service abuse
How Zscaler stops encrypted threats
The Zscaler Zero Trust Exchange offers a robust resolution to stopping encrypted threats, beginning with eliminating blind spots through its TLS/SSL inspection capabilities and AI-driven defenses. Right here’s how Zscaler tackles encrypted threats at each stage of an assault.
Decrease the assault floor: Unchecked encrypted connections, comparable to these by means of VPNs or uncovered workloads, can broaden the assault floor and permit attackers to cover in plain sight. Zscaler eliminates this threat and the assault floor by holding purposes and providers invisible to the web. This method stops encrypted threats from reaching essential purposes and methods, offering proactive safety that doesn’t depend on shared community entry.
Forestall preliminary compromise Zscaler Internet Access™ (ZIA) performs full TLS/SSL inspection to confirm each connection and cease hidden threats with out sacrificing efficiency. ZIA’s inspection capabilities leverage AI-powered evaluation and inline detection to shortly determine and block refined threats inside encrypted visitors. This method eliminates the necessity for conventional, resource-intensive bodily home equipment, permitting organizations to deal with encrypted visitors development simply and with out disruption.
Get rid of lateral motion: Attackers usually intention to maneuver laterally inside networks as soon as they achieve entry. Zscaler prevents this with zero belief segmentation and AI-powered, context-aware insurance policies delivered by means of Zscaler Private Access™ (ZPA). ZPA enforces granular entry controls, limiting customers to particular purposes primarily based on identification, context, and coverage. This replaces complicated rule-based community segmentation with streamlined, identity-based entry management. Moreover, Zscaler makes use of deception technology, setting decoys to detect and thwart lateral motion makes an attempt inside encrypted visitors.
Block command-and-control callbacks Malware usually depends on encrypted channels to speak with C2 servers, enabling attackers to execute instructions, obtain further malware, or exfiltrate delicate knowledge. ZIA inspects outgoing (northbound) and incoming (southbound) encrypted visitors to disrupt C2 communications. Zscaler’s AI-powered data loss prevention tools detect and block malicious visitors, stopping delicate knowledge from being exfiltrated and encrypted C2 callbacks from compromising the community.
Case examine: Learn the way Wipro blocked 8.2M encrypted threats in a single quarter with Zscaler
By changing conventional firewalls and VPNs with Zscaler, Wipro strengthened its defenses with inline TLS/SSL inspection of all web and SaaS visitors to detect and block encrypted threats. Learn their story here.
Why complete TLS/SSL inspection issues
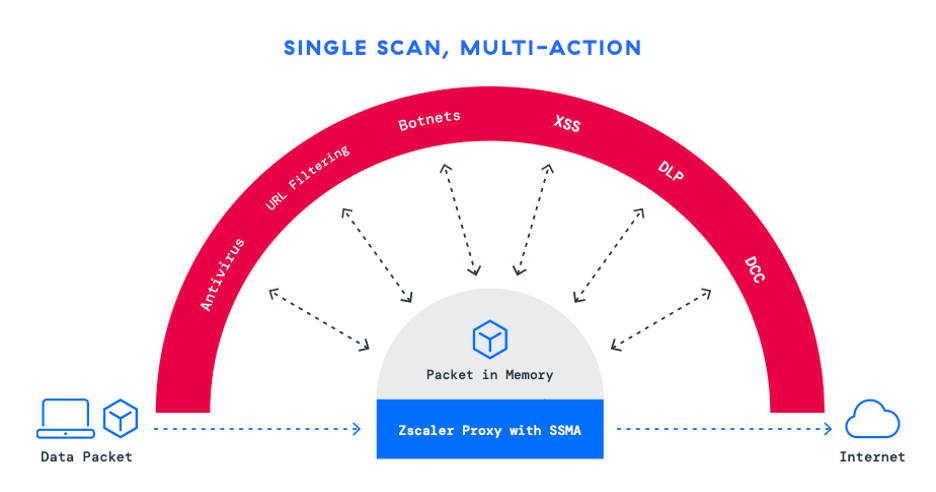
The inspiration of Zscaler’s protection in opposition to encrypted threats is its full TLS/SSL inspection capabilities, enabled by a scalable proxy-based structure. Not like conventional hardware-based options that pressure organizations to compromise between safety and pace, Zscaler’s cloud-native method permits organizations to completely examine visitors at scale with its Single Scan, Multi-Motion engine—a singular characteristic that processes visitors as soon as to use a number of safety controls concurrently. This helps organizations to:
- Examine 100% of encrypted visitors: Not like options that examine solely a fraction of encrypted visitors resulting from {hardware} constraints, Zscaler’s cloud-native structure ensures each packet is inspected with out exception.
- Layer superior safety controls: Inline, AI-powered safety controls detect and block threats embedded in encrypted visitors.
- Keep excessive efficiency: Zscaler’s structure eliminates bottlenecks usually related to {hardware} home equipment.
Zscaler
Keep forward of encrypted threats
The findings within the ThreatLabz 2024 Encrypted Attacks Report make it clear that risk actors are constantly evolving with the assistance of encryption and AI applied sciences to evade detection and maximize their influence.
Dive deeper into the newest analysis and study extra about how one can keep forward of encrypted threats. The complete report affords:
- In-depth evaluation: Detailed findings and case research on how attackers are leveraging encryption.
- 2025 predictions: Knowledgeable insights into the place the encrypted risk panorama is headed.
- Actionable finest practices: A sensible guidelines for enhancing your defenses in opposition to encrypted assaults.
Shield your group from encrypted threats. Get your copy of the report right now.




