Tag: flaw
Cisco finally patches seven-week-old zero-day flaw in Secure Email Gateway products
“Talos assesses with average confidence that this exercise is being performed by a Chinese language-nexus risk actor, which…
Palo Alto Networks patches firewalls after discovery of a new denial-of-service flaw
This new vulnerability brings to thoughts an nearly similar Palo Alto Networks DoS concern from late 2024, CVE-2024-3393,…
Azure Entra ID Flaw Highlights Microsoft IAM Issues
A crucial Microsoft authentication vulnerability may have allowed a menace actor to compromise just about each Entra ID…
AMI MegaRAC authentication bypass flaw is being exploitated, CISA warns
The spoofing assault works by manipulating HTTP request headers despatched to the Redfish interface. Attackers can add particular…
As clock ticks, vendors slowly patch critical flaw in AMI MegaRAC BMC firmware
Dell, alternatively, has confirmed that its techniques are unaffected by the MegaRAC concern, because it makes use of…
Ivanti warns customers of new critical flaw exploited in the wild
“The vulnerability is a buffer overflow with a restricted character area, and subsequently it was initially believed to…
Attackers probing backdoor flaw in popular Cisco Smart Licensing Utility, warns SANS
Backdoor secrecy The hardcoded password flaw, recognized as CVE-2024-20439, could possibly be exploited to attain administrator privileges through…
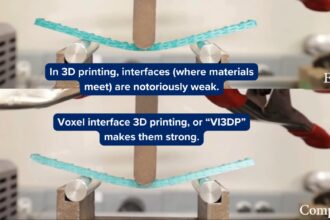
Turning 3D printing’s biggest flaw into its smartest feature
Credit score: Johns Hopkins College Civil and techniques engineers at Johns Hopkins College have turned a longstanding downside…
Cisco IoT wireless access points hit by severe command injection flaw
In a 2021 weblog concerning the know-how, Fluidmesh Community’s co-founder and former CEO Umberto Malesci gave several examples…
Researcher reveals ‘catastrophic’ security flaw in the Arc browser
Arc has a function known as Boosts that lets you customise any web site with customized CSS and…
Should enterprises be concerned about Intel’s crashing CPU flaw?
In response to Nguyen, firm’s latest actions — lowering their workforce by 15% and eliminating “non-essential” exercise —…
Cisco patches actively exploited zero-day flaw in Nexus switches
Cisco has launched patches for a number of collection of Nexus switches to repair a vulnerability that would…