Tag: CISOs
Software is 40% of security budgets as CISOs shift to AI defense
Need smarter insights in your inbox? Join our weekly newsletters to get solely what issues to enterprise AI,…
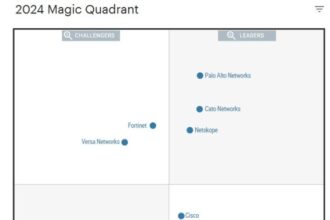
Facing AI-powered threats, CISOs consolidate around single-vendor SASE
Need smarter insights in your inbox? Join our weekly newsletters to get solely what issues to enterprise AI,…
Databricks, Noma Tackle CISOs’ AI Inference Nightmare
Be part of the occasion trusted by enterprise leaders for practically twenty years. VB Remodel brings collectively the…
RSAC 2025: Why the AI agent era means more demand for CISOS
Be a part of our each day and weekly newsletters for the most recent updates and unique content…
Shadow AI: The hidden security breach CISOs often miss
Be a part of our day by day and weekly newsletters for the most recent updates and unique…
AMD’s unpatched chip microcode glitch may require extreme measures by CISOs
“If a system is compromised to this degree, the power to deploy malicious microcode to the CPU may…
CISOs who delayed patching Palo Alto vulnerabilities now face real threat
“Palo Alto Networks has noticed menace exercise exploiting an unauthenticated distant command execution vulnerability in opposition to a…
A CISO’s Observations on Today’s Rapidly Evolving Cybersecurity Landscape
There's a troublesome disconnect between many enterprise leaders and their cybersecurity groups. The previous nonetheless believes there's such a factor…
From the trenches: A CISO’s guide to threat intelligence
Let’s face it, our jobs as CISOs are a relentless dance with the shadows. We combat invisible enemies,…
SEC Cyber Disclosure Rules Usher in a New Era for CISOs | DCN
In response to increasingly sophisticated cyber threats and data leaks, the Securities and Exchange Commission has taken a…