Firewalls and proxies aren’t the flashiest IT matters, however they’re the silent guardians of your group’s cloud and on-premises environments. Consider them because the gatekeepers, deciding who will get in and stays out.
Like most safety instruments, their effectiveness relies upon not solely on their options but additionally on how effectively organizations handle and configure them. Maintain studying to find actionable methods for enhancing safety and effectivity.
Managing North-South, East-West Site visitors
A typical enterprise community consists of a number of zones for workspaces, utility servers, databases, and extra. Exterior firewalls management the visitors between these zones and the web, sometimes known as ‘north-south visitors.’
In distinction, “east-west visitors” represents the circulation between inner zones ruled by inner firewalls (see Determine 1). Whereas proxies primarily handle outbound visitors from office zones to the web, bigger organizations may additionally use them for server visitors.
Determine 1: Pattern Community Setup
Determine 1: Pattern Community Setup
Organizations can cut back their community assault floor by tailoring rule units. Even a easy setup can embody quite a few zone-specific insurance policies. For instance, database servers sometimes don’t want web entry. Thus, the firewall rule set for database zones blocks all outgoing connectivity whereas allowing incoming JDBC/ODBC connections from utility zones.
Why Controls for Egress Site visitors?
Whereas community safety usually focuses on preserving threats out, contemplate the situation the place an intruder is already contained in the community. Egress controls – by way of firewalls or proxies – forestall information exfiltration and cease contaminated servers from reaching command-and-control facilities. They function the final line of protection, curbing an assault earlier than it escalates right into a full-blown catastrophe.
Managing Proxy and Firewall Modifications
Firewall and proxy administration follows a easy rule: block all ports by default and permit solely important visitors. Recognizing that builders perceive their purposes finest, why not empower them to handle firewall and proxy modifications as a part of a “shift safety left” technique? In apply, nonetheless, tight deadlines usually lead builders to implement overly broad connectivity – opening as much as the whole web – with plans to refine later. Non permanent fixes, if left unchecked, can evolve into severe vulnerabilities.
Each safety specialist understands what occurs in apply. When deadlines are tight, builders could also be tempted to take shortcuts. As a substitute of determining the precise wanted IP vary, they open connectivity to your complete web with the intention of fixing this later. Options that had been meant to be non permanent usually accumulate, creating vital safety vulnerabilities over time.
To mitigate this danger, mature organizations sometimes undertake two practices:
-
Formal safety approval by the CISO group for (sure) modifications and
-
Centralizing the implementation of firewall and proxy rule set modifications.
Some organizations schedule weekly or biweekly change board conferences for such approvals and have outlined implementation dates for these modifications.
Whereas such a course of helps preserve safety, it additionally introduces delays – particularly if utility groups don’t get change requests proper the primary time and should submit them repeatedly, probably dropping weeks.
Submit-Implementation Rule Set Audits
Periodically auditing firewall and proxy rule units is crucial to sustaining safety, however it isn’t an alternative choice to a sturdy approval course of. Firewalls and proxies are uncovered to exterior threats, and attackers would possibly exploit misconfigurations earlier than periodic audits catch them.
Blocking insecure connections on a firewall when the appliance is already reside requires re-architecting the answer, which is dear and time-consuming. Thus, stopping dangerous modifications should be the precedence.
A Smoother, Quicker Stream: Automating Approvals
One of many largest challenges is balancing velocity with safety. Each pending firewall or proxy change can delay crucial initiatives. The doable enhancements rely upon a change’s danger degree:
-
Excessive-risk: Modifications like distant desktop protocol (RDP) entry from the web are (practically) all the time denied, no matter a challenge’s significance.
-
Medium-risk: Uncommon requests (e.g., UDP protocols for Skype) or extensive IP vary openings require scrutinizing by the safety crew.
-
Low-risk: Requests like HTTPS visitors to net purposes or purposes connecting to databases by way of JDBC are commonplace. There isn’t a want for safety validation.
Expediting medium- and high-risk choices is difficult. If there’s funds, assigning extra workers is an effective possibility. Growing the danger urge for food and performing extra superficial checks is the opposite different.
For low-risk modifications, combining and automating approvals and alter implementations considerably velocity up the method with out compromising safety. The prerequisite is that the safety group defines clear standards for what constitutes a low-risk change.
Then, the cloud platform crew can implement a Firewall and Proxy Modifications API, as Determine 2 illustrates. When an utility crew requests a change, the API checks whether or not this requestor has the mandatory function, e.g., based mostly on useful resource tags.
Subsequent, the API checks whether or not the change meets the group’s standards for low-risk modifications (e.g., JDBC to a database). If that’s the case, the API deploys the change instantly, although it is dependent upon the cloud supplier how rapidly the change takes impact.
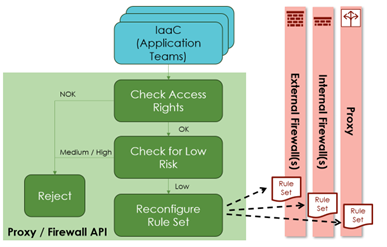
Determine 2: Self-service firewall and proxy modifications for utility groups by way of an API
Determine 2: Self-service firewall and proxy modifications for utility groups by way of an API
One other strategy is to break up tasks for community safety parts by having two complimentary controls, as Determine 3 illustrates.
For example, two complementary controls could be a firewall of the hub community zone and the firewall on the spoke zone – or the Azure Firewall versus Azure Community Safety Teams (NSGs). If each side open the port, visitors is feasible.
The concept for implementing the break up is that solely the central crew manages the medium and high-risk ports (all the time open on the opposite facet), whereas the appliance groups management the settings for the low-risk ports.
Each the API-driven strategy and the split-responsibility mannequin require integration with change administration processes to take care of complete audit trails.
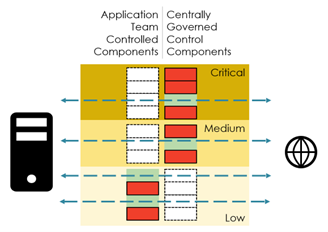
Determine 3: Implementing self-service with break up tasks
Determine 3: Implementing self-service with break up tasks
The Take Residence Message
Efficient firewall and proxy administration is about balancing freedom and safety – empowering engineers to maintain initiatives shifting whereas safeguarding the community. With improvements in Infrastructure as Code (IaC), public cloud providers, and automation, organizations can streamline low-risk modifications, decreasing bureaucratic delays with out sacrificing safety.
Placing the precise steadiness ensures a safe, agile utility panorama – one resilient towards evolving cyber threats.




