Software Programming Interfaces (APIs) are the inspiration of enterprise course of automation and environment friendly inter-company collaboration, however in addition they introduce new and distinctive safety dangers.
Regardless of sturdy implementation patterns, many organizations depend on outdated practices, comparable to static, decades-old passwords for exterior APIs. This presents the basic dilemma: tangible prices for enhancing API safety versus summary cyber dangers. Thus, aligning technical enhancements with enterprise enterprise dangers is the important thing to securing funding for these initiatives, and this text explains the mechanics.
Understanding Enterprise Safety Dangers
Previous to initiating any engineering work, organizations should prioritize their safety dangers. A danger matrix is crucial for this enterprise and visualizes and ranks dangers based mostly on two dimensions (Determine 1):
-
Severity: The potential penalties of an occasion or incident (e.g., a $300,000 loss).
-
Probability: The chance of a danger materializing (e.g., as soon as in 10 years).
Severity has many sides, from direct income loss and fines to staff who can not carry out their work. Severity additionally covers features with out direct monetary affect, together with potential affect on model popularity, regulator interventions, or actions of information privateness places of work. The evaluation of severity extremely is dependent upon a corporation’s context, such because the business sector, its monetary stability, and measurement.
Determine 1: A pattern danger matrix for a big enterprise
Making use of Danger Matrices to API Safety
A convincing enterprise case for enhancing API safety begins with mapping dangers onto a corporation’s danger matrix. APIs want a ranking, both individually or in courses, based mostly on their knowledge or enterprise function. For the severity dimension, the main focus is on the potential penalties of an API compromise. Would attackers acquire entry to affected person knowledge in hospitals or rocket development plans, or just footage of a web based webshop? May they provoke cash transfers or intrude with prepare or air site visitors management techniques?
The chance dimension, nonetheless, is more difficult. If an API had an incident this yr and one other two years in the past, no person realistically disputes a ranking “typically.” Nevertheless, there may be typically (luckily) no supporting historic knowledge. Then, rankings would possibly spark debate. Some would possibly argue that if nothing has ever occurred, the chance have to be zero indefinitely – which is clearly flawed reasoning.
A sensible strategy right here is just not to have a look at particular person APIs however to evaluate the underlying API safety sample. The sample “entry key with out periodic key rotation” would possibly set off a chance ranking of “typically,” whereas combining a VPN tunnel with OAuth could be rated as “seldom.”
Acceptable and Unacceptable Dangers
Discovering funding for API safety enhancements is easy if a cost-benefit evaluation demonstrates a optimistic return on funding (ROI).
Think about a cost API with an estimated breach chance of as soon as each 5 years, with every breach leading to damages of $500,000. On this case, spending $10,000 yearly to implement, monitor, and keep a safer API brings clear monetary advantages if the chance of a breach is diminished to as soon as in 50 years.
Sadly, such compelling enterprise instances are uncommon. Most cybersecurity tasks observe a special logic: cut back the chance degree from unacceptable to acceptable. The danger matrix formalizes a corporation’s danger urge for food on this context, serving to to distinguish between acceptable and unacceptable dangers.
In Determine 1, API A has the severity “excessive” and the chance “sure,” ensuing within the classification as “black.” That is an unacceptably excessive danger for this enterprise, requiring an enchancment of this API’s safety. API B, nonetheless, is “inexperienced” and throughout the group’s danger urge for food. API C is “purple.” The senior administration should both formally settle for the chance or put money into enhancing the safety of this API.
How you can Decrease API Safety Dangers
There are two methods for addressing excessive API-related dangers: decreasing the potential affect of an API-related safety incident and decreasing the chance of such occasions. Lowering the chance is a technique corresponding with “transferring up” within the danger matrix, as depicted by arrow A in Determine 2 (under).
One possibility is enhancing the authentication mechanisms by changing entry keys with certificates or certificates with managed workload identities. Strengthening network-level safety, comparable to routing site visitors to APIs by way of VPN tunnels, is one other efficient possibility.
Operational enhancements are a non-technical, although efficient, different to decreasing the chance of API-related safety incidents. Limiting who can entry certificates or implementing a four-eyes precept for security-critical API adjustments are two examples of operational changes. These measures cut back the chance of intentional and unintended misconfigurations.
Alternatively, organizations can shift left within the danger matrix, thereby decreasing the chance by limiting the potential affect of incidents. Varied methods will be employed on this context. For example, a cost API might monitor for anomalies, comparable to a sudden 50% enhance in outgoing funds, and quickly halt additional funds to permit for investigation. Different potential measures embody eradicating delicate private knowledge and even all private figuring out knowledge from APIs – each decrease the chance ranking for APIs, for which knowledge safety and privateness are the first safety considerations.
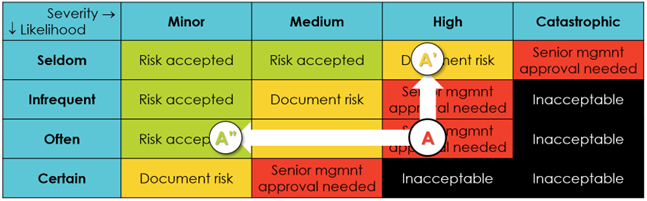
Determine 2: Danger discount methods
API Safety and Safe Software program Engineering
Particular person assessments are ample for giant tasks and legacy APIs. Nevertheless, long-lasting success is dependent upon designing APIs with correct safety from the start. Two key preparatory actions, constructing on the ideas mentioned to date, are the premise for clearly defining directions for builders.
The primary preparatory motion is defining easy guidelines for the criticality of an API. For instance, if an API retrieves gross sales knowledge for particular person prospects with automated throttling for greater than 10 requests per minute, its incident severity could be categorized as ”medium”. If the API supplies full buyer lists with full CRM knowledge, the Incident severity is “excessive” (Determine 3).
The second preparatory prerequisite is assessing safety patterns for the chance of an incident or breach. For instance, an organization would possibly charge entry keys with rotation as “typically,” certificates as “rare,” and VPN tunnels with mutual Transport Layer Safety (mTLS) as “seldom.” With a danger urge for food of “orange,” an API for particular person buyer knowledge should implement entry keys with rotation. Static passwords wouldn’t be enough, and VPN tunnels could be an overinvestment. This strategy allows clear guidelines for builders as Determine 3 illustrates.
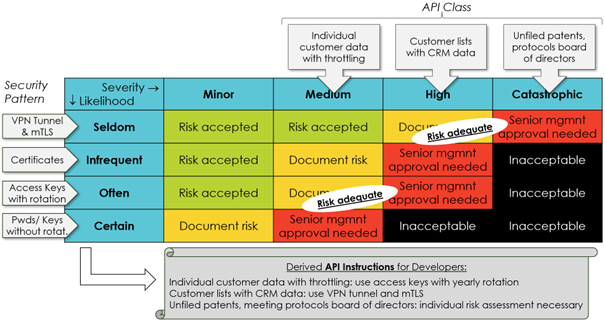
Determine 3: Deriving guidelines for builders
Conclusion
In at this time’s digital panorama, engineers and safety specialists want to know extra than simply the technical facet of API safety. They have to align a corporation’s danger urge for food with the dangers of the present or envisioned API safety patterns.
On this endeavor, a danger matrix is a key device each engineer and safety specialist should know and perceive tips on how to apply.




