The position of the CISO continues to develop, pushed by the rising variety of breaches and cyberattacks like ransomware, in addition to SEC necessities for public organizations to reveal materials breaches.
Among the many fastest-moving frontiers in enterprise cybersecurity: cellular, the web of issues (IoT), and operational expertise (OT) programs. As we speak, 96.5% of individuals entry the web with a cellular gadget, whereas 59% of web site visitors is generated by cellular units. In the meantime, OT and cyber-physical programs, as soon as air-gapped and remoted from the web, have quickly turn out to be built-in into enterprise networks, the place threats can proliferate.
To make clear this burgeoning menace panorama, the Zscaler ThreatLabz analysis staff carried out an in depth evaluation of cellular and IoT/OT assault traits from June 2023 to Might 2024.
Total, ThreatLabz tracked an increase in financially motivated cellular assaults – with 111% progress in adware and 29% progress in banking malware – most of which might bypass multifactor authentication (MFA). In the meantime, IoT assaults grew 45% year-over-year, and ThreatLabz recognized pervasive safety dangers in OT environments.
Under, we’ll summarize key findings from the report. For a complete understanding of cellular and IoT/OT traits, case research, and greatest practices to safe your group, obtain the Zscaler ThreatLabz 2024 Mobile, IoT, and OT Threat Report.
Prime Cellular and IoT/OT traits
- Rise in financially-motivated cellular threats, together with a 111% rise in adware and 29% progress in banking malware.
- Regardless of an general lower in Android assaults, financially-motivated cellular threats are rising, with the bulk in a position to bypass MFA.
- IoT assaults elevated by 45% primarily based on blocked makes an attempt within the Zscaler cloud in comparison with our 2023 report.
- Zscaler blocked 45% extra IoT malware transactions than the earlier 12 months. ThreatLabz additionally noticed a 12% rise within the variety of makes an attempt to ship malware (payload deliveries) to IoT units.
- ThreatLabz found 200+ pretend apps on the Google Play Retailer.
- This contains Anatsa, a recognized Android banking malware that has focused greater than 650 monetary establishments through the use of PDF and QR code readers to distribute itself.
- Legacy and end-of-life working programs (OS) go away OT programs weak.
- Previousy air-gapped and remoted from the web, OT and cyber-physical programs are quickly turning into built-in into enterprise networks, enabling threats to proliferate.
- In an evaluation of large-scale OT deployments ThreatLabz discovered 50% or extra of OT programs use an end-of-life OS, many with recognized vulnerabilities. In the meantime, dangerous protocols and companies in east-west OT site visitors abound.
Prime cellular and IoT/OT targets
5. India was the highest goal for cellular assaults, experiencing 28% of all assaults, adopted by the US, Canada, South Africa, and the Netherlands. America stays the highest goal of IoT assaults, experiencing 81% of all assaults, adopted by Singapore, the UK, Germany, and Canada.
Zscaler
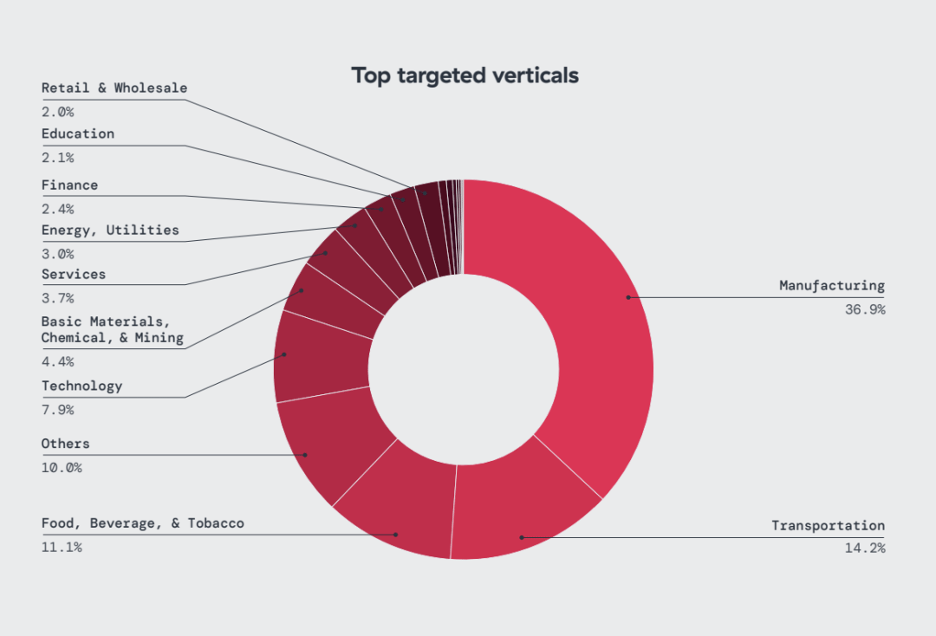
6. Manufacturing skilled the best quantity of IoT assaults, accounting for 36% of all IoT malware blocks noticed, adopted by transportation (14%) and meals, beverage & tobacco (11%). The expertise and training sectors have been most focused by cellular threats.
Zscaler
Securing cellular, IoT, and OT with zero belief
As cyberattacks that focus on cellular and IoT/OT property turn out to be extra subtle, enterprises want a option to cut back cyber threat whereas embracing IoT and OT connectivity to drive enterprise. Certainly, not solely are IoT assaults rising, however menace actors are actively focusing on OT units and demanding infrastructure, about which CISA has warned. In the meantime, enterprises want a option to robustly safe cellular connectivity to any SaaS or non-public software, whether or not within the cloud or within the information heart. To guard these units and programs, enterprises ought to undertake a zero belief method that mitigates cyberthreats and improves their safety posture:
- Uncover, classify, and stock IoT and OT property: Work to achieve full visibility into your IoT and OT assault floor; this contains discovering, classifying, and inventorying each managed and unmanaged or “shadow” units. With this type of holistic view, defenders can prioritize their efforts, determine key vulnerabilities, and develop a proactive method to securing these property.
- Allow zero belief connectivity: Leverage a sturdy zero belief structure that permits adaptive entry choices primarily based on the real-time safety and posture of consumer units, threat components, and gadget telemetry, making certain safe direct connectivity between endpoints and purposes – by no means to the underlying community.
- Implement zero belief gadget segmentation: Apply least-privileged entry controls for device-to-application, user-to-application, and application-to-application segmentation. This granular degree of segmentation eliminates lateral motion, minimizes information publicity, and strengthens your general safety posture by decreasing the potential for a single compromised gadget to jeopardize all the community. This could embrace isolating and totally segmenting agentless IoT/OT units right into a safe “community of 1,” together with legacy servers and headless machines.
- Keep constant zero belief safety insurance policies: Make sure that zero belief entry insurance policies are constantly enforced throughout all environments, whether or not customers are at headquarters, model places, or accessing purposes remotely.
As cellular and IoT/OT threats proliferate, it’s vital to grasp the newest traits, the implications of those sorts of assaults, and the best-practice methods you’ll be able to undertake to safe your group in opposition to a full vary of threats.
Get your copy of the Zscaler ThreatLabz 2024 Mobile, IoT, and OT Threat Report right this moment.




